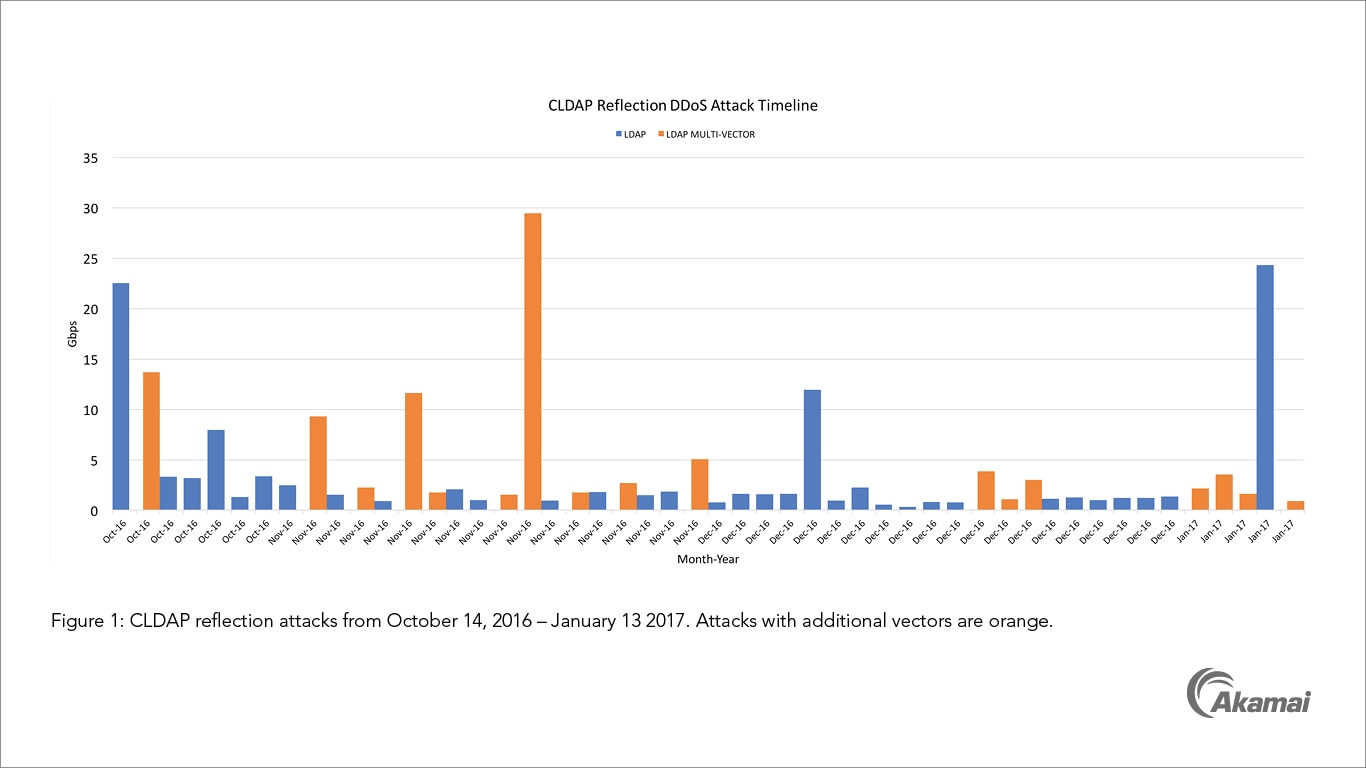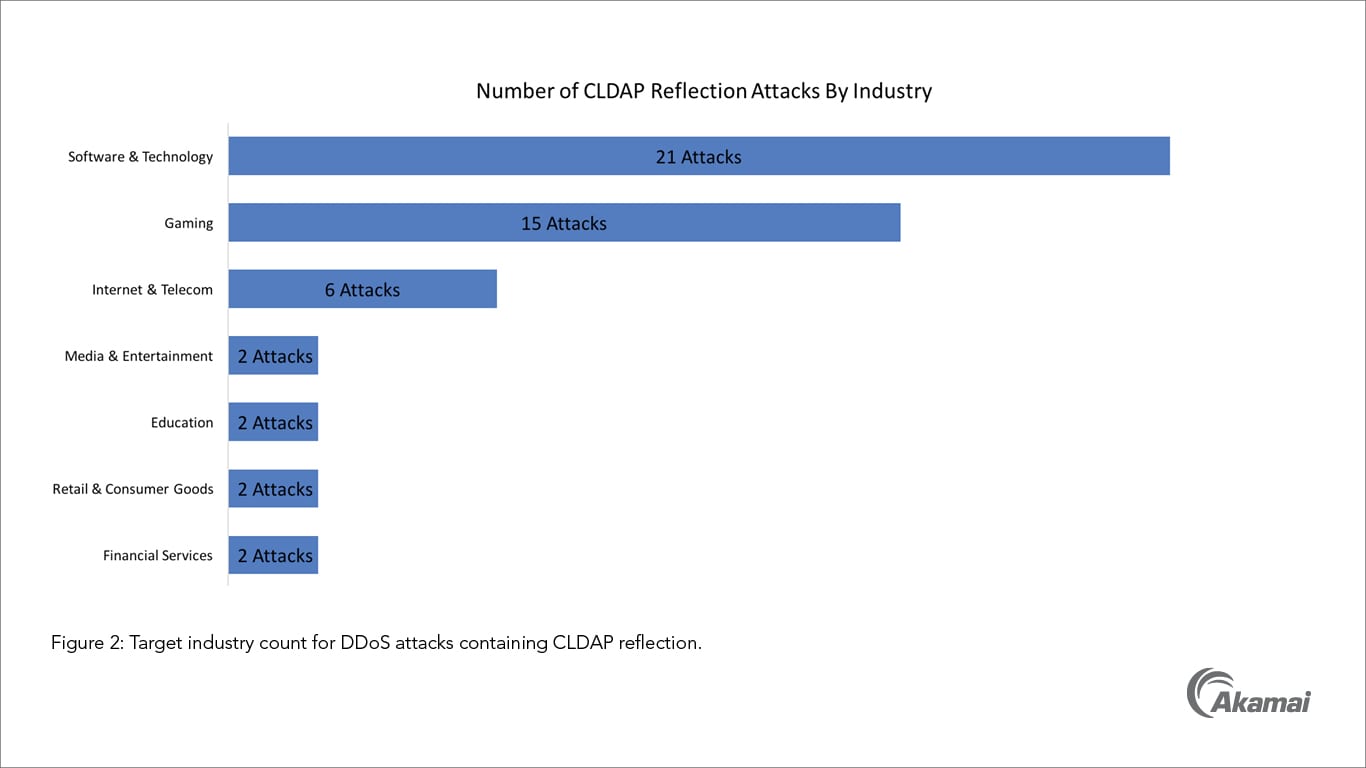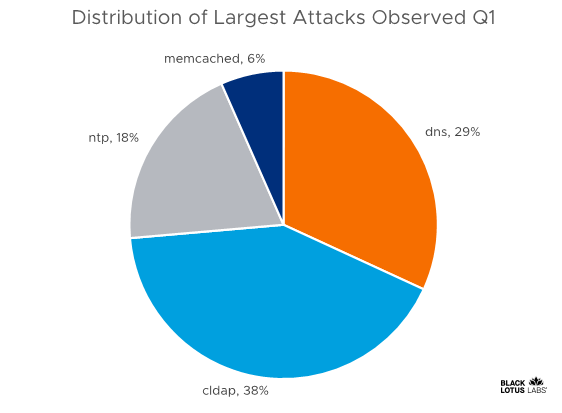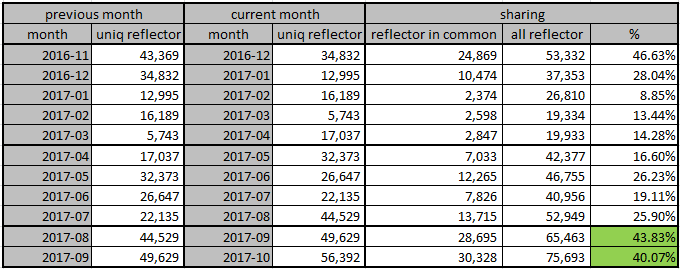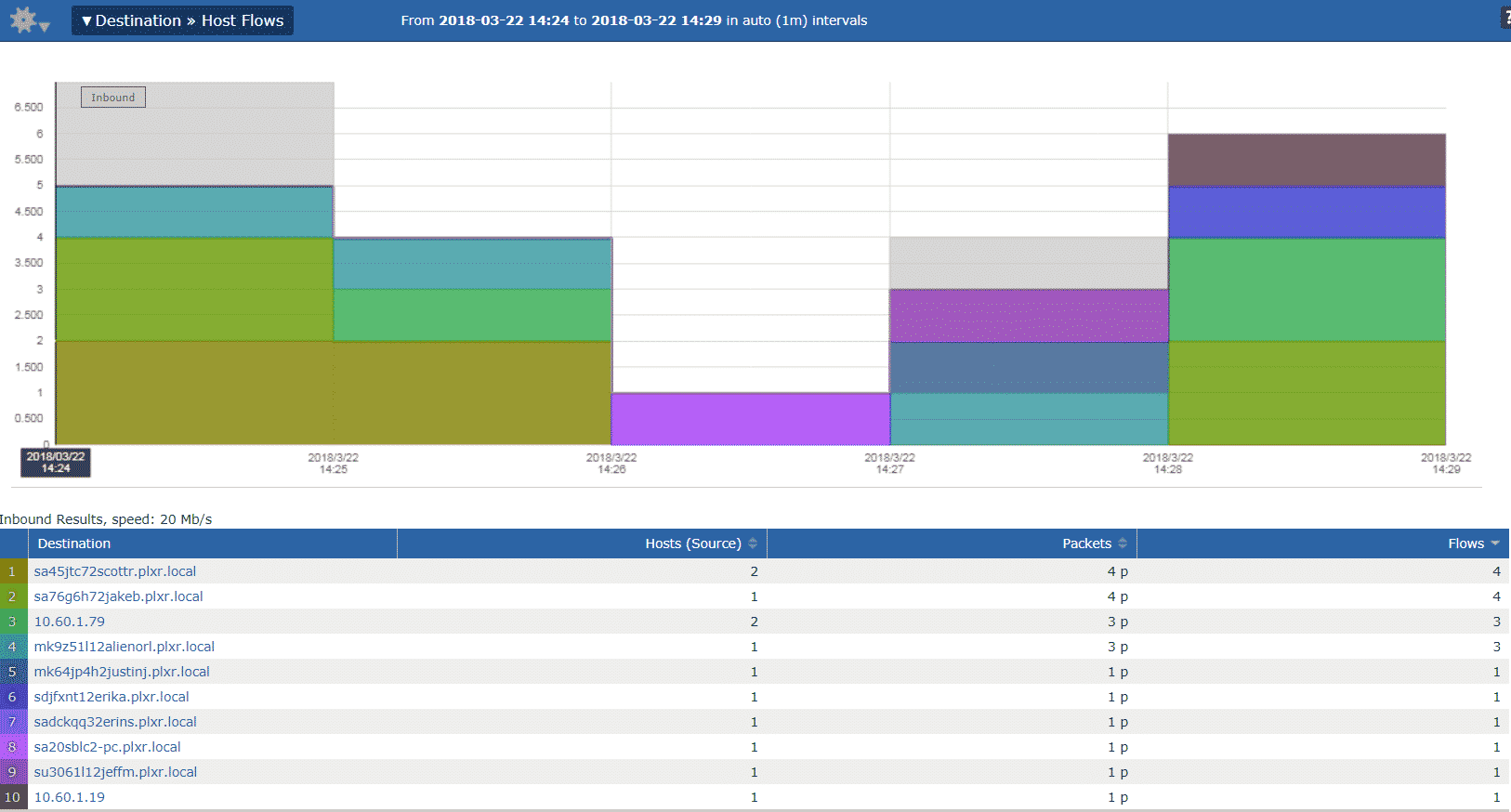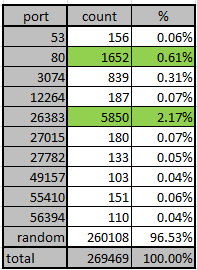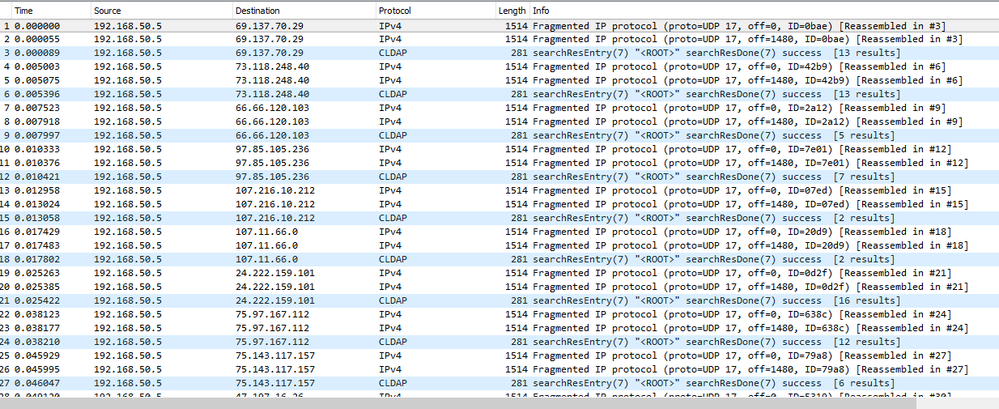
Possible CLDAP DDoS - But how is traffic coming from outside to inside with no open ports or NAT to ... - Cisco Community

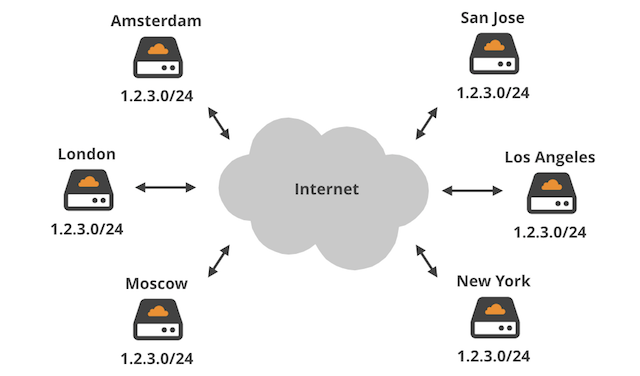
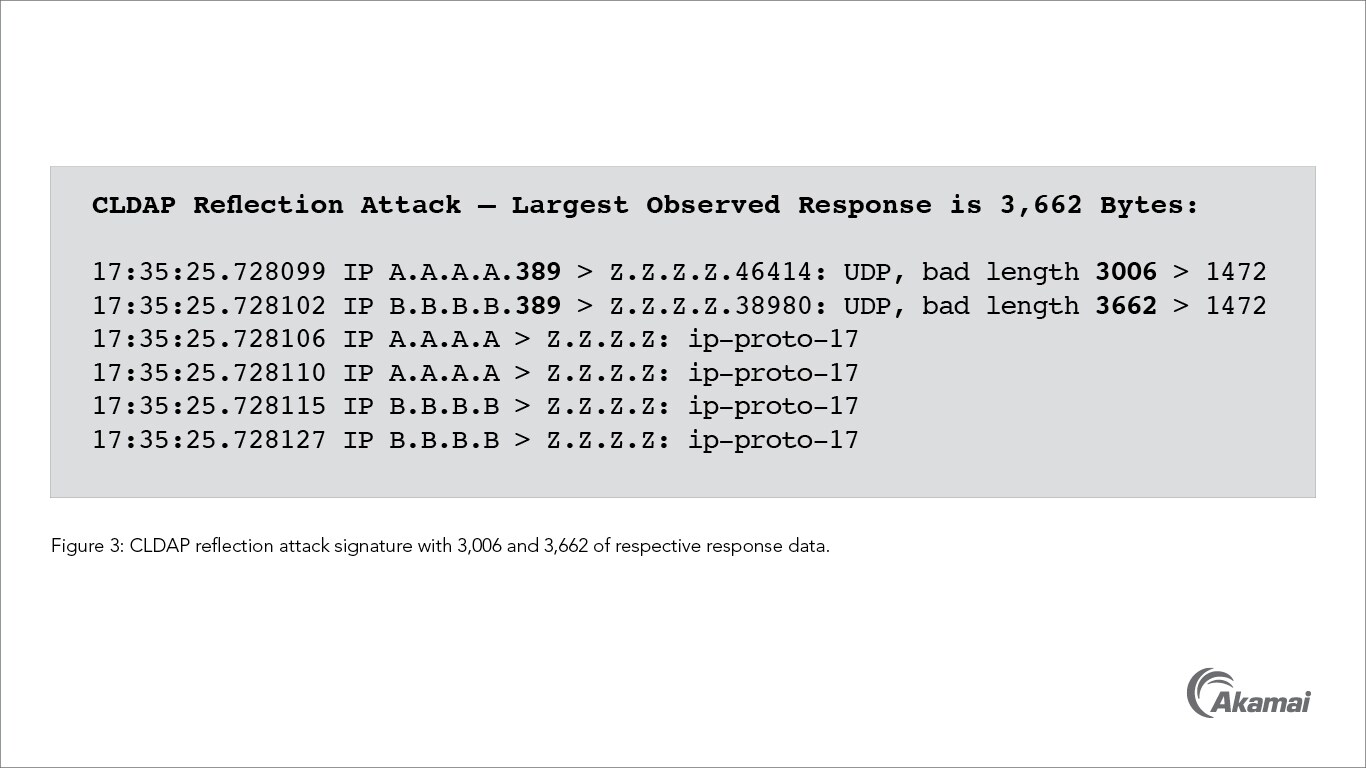
CLDAP Reflection Attacks back in style for the spring 2020 collection | DOSarrest Internet Security| DDoS Protection

Possible CLDAP DDoS - But how is traffic coming from outside to inside with no open ports or NAT to ... - Cisco Community

![AWS DDoS via [CLDAP] AWS DDoS via [CLDAP]](https://media-exp1.licdn.com/dms/image/C4D12AQEldUWkc5Qkpw/article-inline_image-shrink_1000_1488/0/1592870479635?e=1669852800&v=beta&t=SRYYE9RxzcakKqO-Bd0r6VOAv6wNfSE0eT1rC3W19aI)