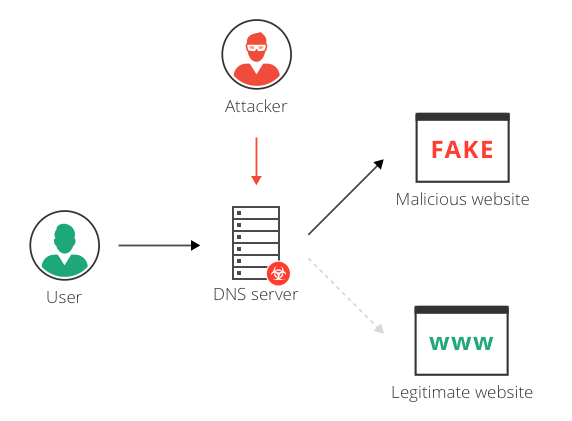
CNN Philippines - Landline and internet service provider PLDT's Twitter account was hacked this afternoon, with hackers demanding better internet services. A group which identified itself as the Legion hackers claimed control

Update Your Netgear Router or Risk Being Hacked - CTC - CTC Fiber Internet to the Home Blog | Ctc Telecom

Picture collage maker pro v3.3.4.3588 final | pratotsak | Wifi hack, Show wifi password, Wifi password






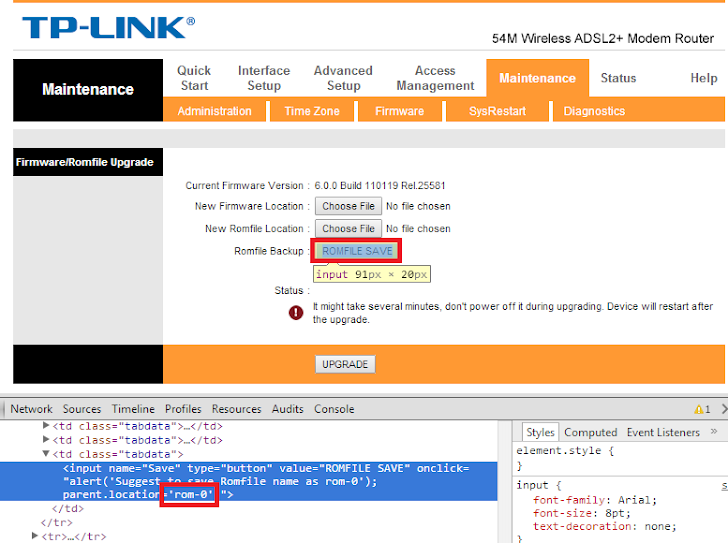



/secure-wireless-network-173875312-5bf25a2046e0fb00262e39fb-bc6c510d1f114a1ab71fa3c96ccbf3ba.jpg)